
This post is part of our ongoing series on running MongoDB on Kubernetes. We’ve published a number of articles about running MongoDB on Kubernetes for specific platforms and for specific use cases. If you are looking for a specific Kubernetes platform, check out these related articles.
Running HA MongoDB on Azure Kubernetes Service (AKS)
Running HA MongoDB on Amazon Elastic Container Service for Kubernetes (EKS)
Running HA MongoDB on Red Hat OpenShift
Running HA MongoDB on Google Kubernetes Engine (GKE)
Running HA MongoDB with Rancher Kubernetes Engine (RKE)
Running HA MongoDB on IBM Cloud Private
Failover MongoDB 300% faster and run only 1/3 the pods
And now, onto the post…
IBM Cloud Kubernetes Service is a managed Kubernetes offering running in IBM Cloud. It is designed to deliver powerful tools, intuitive user experience, and built-in security for rapid delivery of applications that can be bound to cloud services related to IBM Watson, IoT, DevOps and data analytics. As a CNCF certified Kubernetes provider, IBM Cloud Kubernetes Service provides intelligent scheduling, self-healing, horizontal scaling, service discovery and load balancing, automated rollouts and rollbacks, and secret and configuration management. The service also has advanced capabilities around simplified cluster management, container security, and isolation policies, the ability to design a cluster with a custom configuration and integrated operational tools for consistency in deployment.
Portworx is a cloud native storage platform to run persistent workloads deployed on a variety of orchestration engines including Kubernetes. With Portworx, customers can manage the database of their choice on any infrastructure using any container scheduler. It provides a single data management layer for all stateful services, no matter where they run.
This tutorial is a walk-through of the steps involved in deploying and managing a highly available MongoDB cluster on IBM Cloud Kubernetes Service (IKS).
In summary, to run HA MongoDB on IKS you need to:
- Launch an IKS cluster running on bare metal servers with software-defined storage (SDS)
- Install cloud native storage solution like Portworx as a Daemonset on IKS
- Create a storage class defining your storage requirements like replication factor, snapshot policy, and performance profile
- Deploy MongoDB using Kubernetes
- Test failover by killing or cordoning node in your cluster
- Expanding the volume size dynamically
- Perform backup and restore through snapshots
Launching an IKS Cluster
For running stateful workloads in a production environment backed by Portworx, it is highly recommended to launch an IKS cluster based on bare metal servers and software-defined storage. The minimum requirements of a worker node to successfully run Portworx include:
- 4 CPU cores
- 4GB memory
- 128GB of raw unformatted storage
- 10Gbps network speed
For details on launching a Kubernetes cluster with bare metal worker nodes, please refer to the documentation of IBM Cloud Kubernetes Service.
We are using an IKS cluster with 4 nodes out of which 3 nodes are running bare metal servers with SDS based on the instance type ms2c.4x32.1.9tb.ssd.encrypted. Only these machines that meet the prerequisite would be used by Portworx.
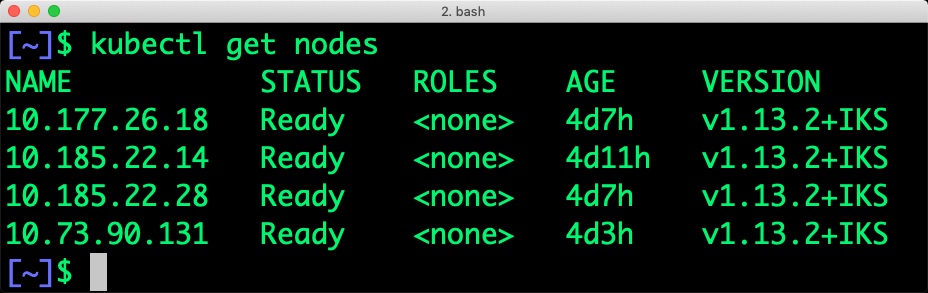
When we filter the nodes based on the label, we see the below nodes:
$ kubectl get nodes -l beta.kubernetes.io/instance-type=ms2c.4x32.1.9tb.ssd.encrypted NAME STATUS ROLES AGE VERSION 10.177.26.18 Ready <none> 4d7h v1.13.2+IKS 10.185.22.28 Ready <none> 4d7h v1.13.2+IKS 10.73.90.131 Ready <none> 4d3h v1.13.2+IKS
To exclude nodes that don’t meet Portworx prerequisites, you can apply a label to skip the installation of Portworx. For example, the below command applies a label on the node with name 10.185.22.14 which doesn’t run on a bare metal server.
$ kubectl label nodes 10.185.22.14 px/enabled=false --overwrite
Installing Portworx in IKS
Installing Portworx on IKS is not very different from installing it on any other Kubernetes cluster. It is recommended that you create an etcd instance through Compose for etcd. You can use the Helm Chart to install Portworx cluster in IKS. Portworx documentation for IKS has the prerequisites and instructions to install and configure Portworx, STORK, and other components.
At the end of the installation, we will have Portworx Daemonset running on the nodes excluding those that are filtered out in the previous step.
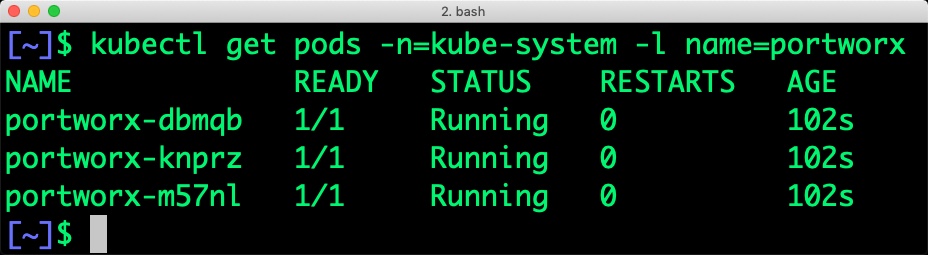
Once the IKS cluster is up and running, and Portworx is installed and configured, we will deploy a highly available MongoDB database.
Creating a storage class for MongoDB
Once the IKS cluster is up and running, and Portworx is installed and configured, we will deploy a highly available MongoDB database.
Through storage class objects, an admin can define different classes of Portworx volumes that are offered in a cluster. These classes will be used during the dynamic provisioning of volumes. The storage class defines the replication factor, I/O profile (e.g., for a database or a CMS), and priority (e.g., SSD or HDD). These parameters impact the availability and throughput of workloads and can be specified for each volume. This is important because a production database will have different requirements than a development Jenkins cluster.
In this example, the storage class that we deploy has a replication factor of 3 with I/O profile set to “db,” and priority set to “high.” This means that the storage will be optimized for low latency database workloads like MongoDB and automatically placed on the highest performance storage available in the cluster.
$ cat > px-mongo-sc.yaml << EOF
kind: StorageClass
apiVersion: storage.k8s.io/v1beta1
metadata:
name: px-ha-sc
provisioner: kubernetes.io/portworx-volume
parameters:
repl: "3"
io_profile: "db_remote"
priority_io: "high"
fs: "xfs"
EOF
Create the storage class and verify its available in the default namespace.
$ kubectl create -f px-mongo-sc.yaml storageclass.storage.k8s.io/px-ha-sc created $ kubectl get sc NAME PROVISIONER AGE default ibm.io/ibmc-file 8d ibmc-file-bronze (default) ibm.io/ibmc-file 8d ibmc-file-custom ibm.io/ibmc-file 8d ibmc-file-gold ibm.io/ibmc-file 8d ibmc-file-retain-bronze ibm.io/ibmc-file 8d ibmc-file-retain-custom ibm.io/ibmc-file 8d ibmc-file-retain-gold ibm.io/ibmc-file 8d ibmc-file-retain-silver ibm.io/ibmc-file 8d ibmc-file-silver ibm.io/ibmc-file 8d portworx-db-sc kubernetes.io/portworx-volume 12h portworx-db2-sc kubernetes.io/portworx-volume 12h portworx-null-sc kubernetes.io/portworx-volume 12h portworx-shared-sc kubernetes.io/portworx-volume 12h px-ha-sc kubernetes.io/portworx-volume 19s px-repl3-sc kubernetes.io/portworx-volume 34h stork-snapshot-sc stork-snapshot 12h
Creating a MongoDB PVC on Kubernetes
We can now create a Persistent Volume Claim (PVC) based on the Storage Class. Thanks to dynamic provisioning, the claims will be created without explicitly provisioning a persistent volume (PV).
$ cat > px-mongo-pvc.yaml << EOF
kind: PersistentVolumeClaim
apiVersion: v1
metadata:
name: px-mongo-pvc
annotations:
volume.beta.kubernetes.io/storage-class: px-ha-sc
spec:
accessModes:
- ReadWriteOnce
resources:
requests:
storage: 1Gi
EOF
$ kubectl create -f px-mongo-pvc.yaml
persistentvolumeclaim/px-mongo-pvc created
$ kubectl get pvc
NAME STATUS VOLUME CAPACITY ACCESS MODES STORAGECLASS AGE
px-mongo-pvc Bound pvc-96a2ff1c-31a9-11e9-930d-4e511e6b17c9 1Gi RWO px-ha-sc 14s
Deploying MongoDB on IKS
Finally, let’s create a MongoDB instance as a Kubernetes deployment object. For simplicity’s sake, we will just be deploying a single Mongo pod. Because Portworx provides synchronous replication for High Availability, a single MongoDB instance might be the best deployment option for your MongoDB database. Portworx can also provide backing volumes for multi-node MongoDB replica sets. The choice is yours.
$ cat > px-mongo-app.yaml << EOF
apiVersion: apps/v1
kind: Deployment
metadata:
name: mongo
spec:
strategy:
rollingUpdate:
maxSurge: 1
maxUnavailable: 1
type: RollingUpdate
replicas: 1
selector:
matchLabels:
app: mongo
template:
metadata:
labels:
app: mongo
spec:
schedulerName: stork
containers:
- name: mongo
image: mongo
imagePullPolicy: "Always"
ports:
- containerPort: 27017
volumeMounts:
- mountPath: /data/db
name: mongodb
volumes:
- name: mongodb
persistentVolumeClaim:
claimName: px-mongo-pvc
EOF
$ kubectl create -f px-mongo-app.yaml deployment.extensions/mongo created
The MongoDB deployment defined above is explicitly associated with the PVC, px-mongo-pvc created in the previous step.
This deployment creates a single pod running MongoDB backed by Portworx.
$ kubectl get pods NAME READY STATUS RESTARTS AGE mongo-6bfc8ccbdc-jcwgg 0/1 ContainerCreating 0 12s
We can inspect the Portworx volume by accessing the pxctl tool running with the Mongo pod.
$ VOL=`kubectl get pvc | grep px-mongo-pvc | awk '{print $3}'`
$ PX_POD=$(kubectl get pods -l name=portworx -n kube-system -o jsonpath='{.items[0].metadata.name}')
$ kubectl exec -it $PX_POD -n kube-system -- /opt/pwx/bin/pxctl volume inspect ${VOL}
Volume : 378818971230765330
Name : pvc-96a2ff1c-31a9-11e9-930d-4e511e6b17c9
Size : 1.0 GiB
Format : ext4
HA : 3
IO Priority : LOW
Creation time : Feb 16 05:13:26 UTC 2019
Shared : no
Status : up
State : Attached: 6ab3face-615f-4cc7-bcfa-a1872d006e34 (10.185.22.29)
Device Path : /dev/pxd/pxd378818971230765330
Labels : pvc=px-mongo-pvc,namespace=default
Reads : 12
Reads MS : 32
Bytes Read : 49152
Writes : 159
Writes MS : 1180
Bytes Written : 18075648
IOs in progress : 0
Bytes used : 1.5 MiB
Replica sets on nodes:
Set 0
Node : 10.73.90.131 (Pool 0)
Node : 10.177.26.18 (Pool 0)
Node : 10.185.22.29 (Pool 0)
Replication Status : Up
Volume consumers :
- Name : mongo-6bfc8ccbdc-jcwgg (bf33a078-31a9-11e9-930d-4e511e6b17c9) (Pod)
Namespace : default
Running on : 10.185.22.29
Controlled by : mongo-6bfc8ccbdc (ReplicaSet)
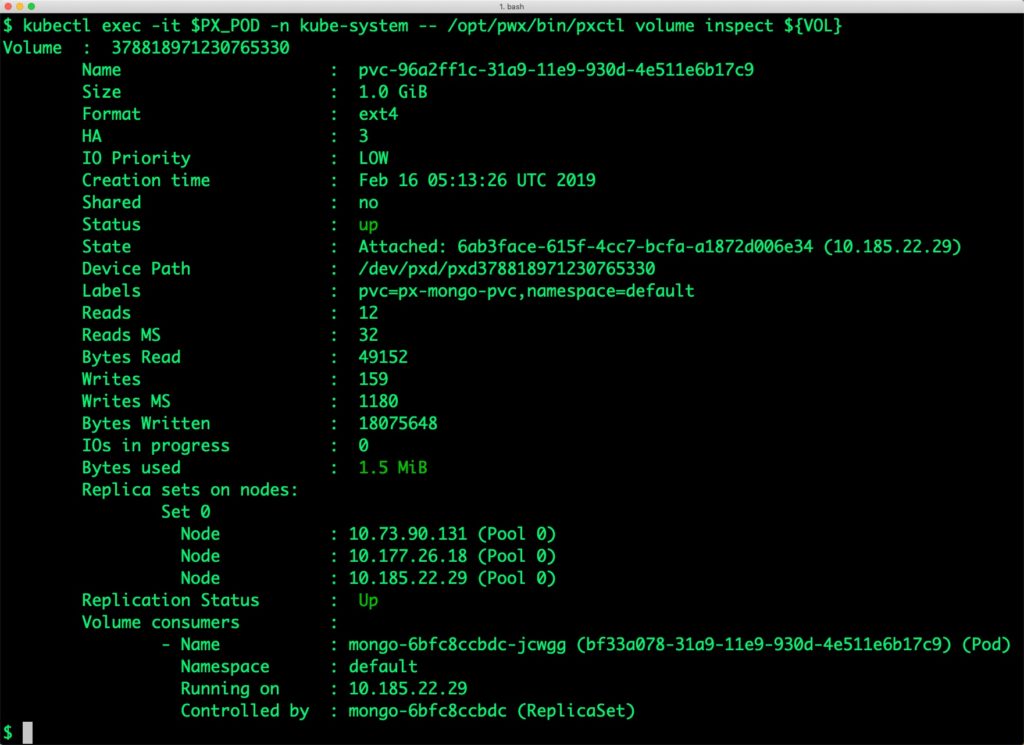
The output from the above command confirms the creation of volumes that are backing MongoDB database instance.
Failing over MongoDB pod on Kubernetes
Populating sample data
Let’s populate the database with some sample data.
We will first find the pod that’s running MongoDB to access the shell.
$ POD=`kubectl get pods -l app=mongo | grep Running | grep 1/1 | awk '{print $1}'`
$ kubectl exec -it $POD mongo
MongoDB shell version v4.0.0
connecting to: mongodb://127.0.0.1:27017
MongoDB server version: 4.0.0
Welcome to the MongoDB shell.
…..
Now that we are inside the shell, we can populate a collection.
db.ships.insert({name:'USS Enterprise-D',operator:'Starfleet',type:'Explorer',class:'Galaxy',crew:750,codes:[10,11,12]})
db.ships.insert({name:'USS Prometheus',operator:'Starfleet',class:'Prometheus',crew:4,codes:[1,14,17]})
db.ships.insert({name:'USS Defiant',operator:'Starfleet',class:'Defiant',crew:50,codes:[10,17,19]})
db.ships.insert({name:'IKS Buruk',operator:' Klingon Empire',class:'Warship',crew:40,codes:[100,110,120]})
db.ships.insert({name:'IKS Somraw',operator:' Klingon Empire',class:'Raptor',crew:50,codes:[101,111,120]})
db.ships.insert({name:'Scimitar',operator:'Romulan Star Empire',type:'Warbird',class:'Warbird',crew:25,codes:[201,211,220]})
db.ships.insert({name:'Narada',operator:'Romulan Star Empire',type:'Warbird',class:'Warbird',crew:65,codes:[251,251,220]})
Let’s run a few queries on the Mongo collection.
Find one arbitrary document:
db.ships.findOne()
{
"_id" : ObjectId("5b5c16221108c314d4c000cd"),
"name" : "USS Enterprise-D",
"operator" : "Starfleet",
"type" : "Explorer",
"class" : "Galaxy",
"crew" : 750,
"codes" : [
10,
11,
12
]
}
Find all documents and using nice formatting:
db.ships.find().pretty()
…..
{
"_id" : ObjectId("5b5c16221108c314d4c000d1"),
"name" : "IKS Somraw",
"operator" : " Klingon Empire",
"class" : "Raptor",
"crew" : 50,
"codes" : [
101,
111,
120
]
}
{
"_id" : ObjectId("5b5c16221108c314d4c000d2"),
"name" : "Scimitar",
"operator" : "Romulan Star Empire",
"type" : "Warbird",
"class" : "Warbird",
"crew" : 25,
"codes" : [
201,
211,
220
]
}
…..
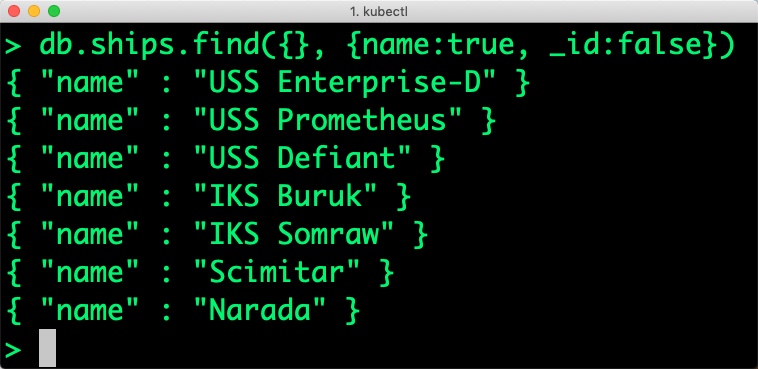
Shows only the names of the ships:
db.ships.find({}, {name:true, _id:false})
{ "name" : "USS Enterprise-D" }
{ "name" : "USS Prometheus" }
{ "name" : "USS Defiant" }
{ "name" : "IKS Buruk" }
{ "name" : "IKS Somraw" }
{ "name" : "Scimitar" }
{ "name" : "Narada" }
Finds one document by attribute:
db.ships.findOne({'name':'USS Defiant'})
{
"_id" : ObjectId("5b5c16221108c314d4c000cf"),
"name" : "USS Defiant",
"operator" : "Starfleet",
"class" : "Defiant",
"crew" : 50,
"codes" : [
10,
17,
19
]
}
Exit from the client shell to return to the host.
Simulating node failure
Now, let’s simulate the node failure by cordoning off the node on which MongoDB is running.
$ NODE=`kubectl get pods -l app=mongo -o wide | grep -v NAME | awk '{print $7}'`
$ kubectl cordon ${NODE}
node/10.185.22.29 cordoned
The above command disabled scheduling on one of the nodes.
$ kubectl get nodes NAME STATUS ROLES AGE VERSION 10.177.26.18 Ready 8d v1.13.2+IKS 10.185.22.14 Ready 8d v1.13.2+IKS 10.185.22.29 Ready,SchedulingDisabled 7h29m v1.13.2+IKS 10.73.90.131 Ready 8d v1.13.2+IKS
Now, let’s go ahead and delete the MongoDB pod.
$ POD=`kubectl get pods -l app=mongo -o wide | grep -v NAME | awk '{print $1}'`
$ kubectl delete pod ${POD}
pod "mongo-6bfc8ccbdc-jcwgg" deleted
As soon as the pod is deleted, it is relocated to the node with the replicated data. STorage ORchestrator for Kubernetes (STORK), a Portworx-contributed open source storage scheduler, co-locates the pod on the exact node where the data is stored. It ensures that an appropriate node is selected for scheduling the pod.
Let’s verify this by running the below command. We will notice that a new pod has been created and scheduled in a different node.
$ kubectl get pods -l app=mongo -o wide NAME READY STATUS RESTARTS AGE IP NODE NOMINATED NODE READINESS GATES mongo-6bfc8ccbdc-cl8nw 1/1 Running 0 13s 172.30.59.94 10.177.26.18
Let’s uncordon the node to bring it back to action.
$ kubectl uncordon ${NODE}
node/10.185.22.29 uncordoned
Finally, let’s verify that the data is still available.
Verifying that the data is intact
Let’s find the pod name and run the ‘exec’ command, and then access the Mongo shell.
$ POD=`kubectl get pods -l app=mongo | grep Running | grep 1/1 | awk '{print $1}'`
$ kubectl exec -it $POD mongo
MongoDB shell version v4.0.0
connecting to: mongodb://127.0.0.1:27017
MongoDB server version: 4.0.0
Welcome to the MongoDB shell.
…..
We will query the collection to verify that the data is intact.
Find one arbitrary document:
db.ships.findOne()
{
"_id" : ObjectId("5b5c16221108c314d4c000cd"),
"name" : "USS Enterprise-D",
"operator" : "Starfleet",
"type" : "Explorer",
"class" : "Galaxy",
"crew" : 750,
"codes" : [
10,
11,
12
]
}
Find all documents and using nice formatting:
db.ships.find().pretty()
…..
{
"_id" : ObjectId("5b5c16221108c314d4c000d1"),
"name" : "IKS Somraw",
"operator" : " Klingon Empire",
"class" : "Raptor",
"crew" : 50,
"codes" : [
101,
111,
120
]
}
{
"_id" : ObjectId("5b5c16221108c314d4c000d2"),
"name" : "Scimitar",
"operator" : "Romulan Star Empire",
"type" : "Warbird",
"class" : "Warbird",
"crew" : 25,
"codes" : [
201,
211,
220
]
}
…..
Shows only the names of the ships:
db.ships.find({}, {name:true, _id:false})
{ "name" : "USS Enterprise-D" }
{ "name" : "USS Prometheus" }
{ "name" : "USS Defiant" }
{ "name" : "IKS Buruk" }
{ "name" : "IKS Somraw" }
{ "name" : "Scimitar" }
{ "name" : "Narada" }
Finds one document by attribute:
db.ships.findOne({'name':Narada'})
{
"_id" : ObjectId("5b5c16221108c314d4c000d3"),
"name" : "Narada",
"operator" : "Romulan Star Empire",
"type" : "Warbird",
"class" : "Warbird",
"crew" : 65,
"codes" : [
251,
251,
220
]
}
Observe that the MongoDB collection is still there and all the content is intact! Exit from the client shell to return to the host.
Performing Storage Operations on MongoDB
After testing end-to-end failover of the database, let’s perform StorageOps on our IKS cluster.
Expanding the Kubernetes Volume with no downtime
Currently, the Portworx volume that we created at the beginning is of 1Gib size. We will now expand it to double the storage capacity.
First, let’s get the volume name and inspect it through the pxctl tool.
$ VOL=`kubectl get pvc | grep px-mongo-pvc | awk '{print $3}'`
$ PX_POD=$(kubectl get pods -l name=portworx -n kube-system -o jsonpath='{.items[0].metadata.name}')
$ kubectl exec -it $PX_POD -n kube-system -- /opt/pwx/bin/pxctl volume inspect ${VOL}
Volume : 378818971230765330
Name : pvc-96a2ff1c-31a9-11e9-930d-4e511e6b17c9
Size : 1.0 GiB
Format : ext4
HA : 3
IO Priority : LOW
Creation time : Feb 16 05:13:26 UTC 2019
Shared : no
Status : up
State : Attached: d7f53ebb-0d02-4ba4-b689-2f335e8f9379 (10.177.26.18)
Device Path : /dev/pxd/pxd378818971230765330
Labels : namespace=default,pvc=px-mongo-pvc
Reads : 50
Reads MS : 84
Bytes Read : 303104
Writes : 486
Writes MS : 3352
Bytes Written : 316612608
IOs in progress : 0
Bytes used : 3.5 MiB
Replica sets on nodes:
Set 0
Node : 10.73.90.131 (Pool 0)
Node : 10.177.26.18 (Pool 0)
Node : 10.185.22.29 (Pool 0)
Replication Status : Up
Volume consumers :
- Name : mongo-6bfc8ccbdc-cl8nw (5da69447-31aa-11e9-930d-4e511e6b17c9) (Pod)
Namespace : default
Running on : 10.177.26.18
Controlled by : mongo-6bfc8ccbdc (ReplicaSet)
Notice the current Portworx volume. It is 1GiB. Let’s expand it to 2GiB.
$ kubectl exec -it $PX_POD -n kube-system -- /opt/pwx/bin/pxctl volume update $VOL --size=2 Update Volume: Volume update successful for volume pvc-96a2ff1c-31a9-11e9-930d-4e511e6b17c9
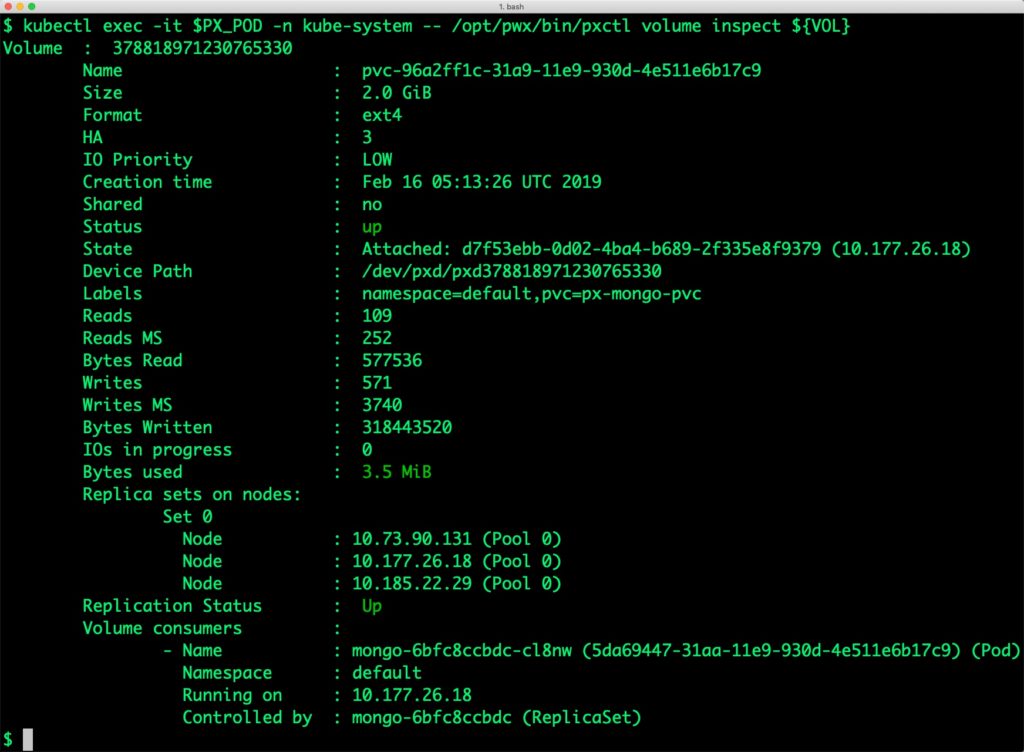
Check the new volume size. It is expanded to 2GiB.
$ kubectl exec -it $PX_POD -n kube-system -- /opt/pwx/bin/pxctl volume inspect ${VOL}
Volume : 378818971230765330
Name : pvc-96a2ff1c-31a9-11e9-930d-4e511e6b17c9
Size : 2.0 GiB
Format : ext4
HA : 3
IO Priority : LOW
Creation time : Feb 16 05:13:26 UTC 2019
Shared : no
Status : up
State : Attached: d7f53ebb-0d02-4ba4-b689-2f335e8f9379 (10.177.26.18)
Device Path : /dev/pxd/pxd378818971230765330
Labels : namespace=default,pvc=px-mongo-pvc
Reads : 109
Reads MS : 252
Bytes Read : 577536
Writes : 571
Writes MS : 3740
Bytes Written : 318443520
IOs in progress : 0
Bytes used : 3.5 MiB
Replica sets on nodes:
Set 0
Node : 10.73.90.131 (Pool 0)
Node : 10.177.26.18 (Pool 0)
Node : 10.185.22.29 (Pool 0)
Replication Status : Up
Volume consumers :
- Name : mongo-6bfc8ccbdc-cl8nw (5da69447-31aa-11e9-930d-4e511e6b17c9) (Pod)
Namespace : default
Running on : 10.177.26.18
Controlled by : mongo-6bfc8ccbdc (ReplicaSet)
Taking Snapshots of a Kubernetes volume and restoring the database
Portworx supports creating snapshots for Kubernetes PVCs.
Let’s create a snapshot of the PVC we created for MongoDB.
cat > px-mongo-snap.yaml << EOF apiVersion: volumesnapshot.external-storage.k8s.io/v1 kind: VolumeSnapshot metadata: name: px-mongo-snapshot namespace: default spec: persistentVolumeClaimName: px-mongo-pvc EOF
$ kubectl create -f px-mongo-snap.yaml volumesnapshot.volumesnapshot.external-storage.k8s.io/px-mongo-snapshot created
Verify the creation of volume snapshot.
$ kubectl get volumesnapshot NAME AGE px-mongo-snapshot 11s
$ kubectl get volumesnapshotdatas NAME AGE k8s-volume-snapshot-51c09f48-31ab-11e9-993d-eaa7125cd4d9 23s
With the snapshot in place, let’s go ahead and delete the database.
$ POD=`kubectl get pods -l app=mongo | grep Running | grep 1/1 | awk '{print $1}'`
$ kubectl exec -it $POD mongo
db.ships.drop()
Since snapshots are just like volumes, we can use it to start a new instance of MongoDB. Let’s create a new instance of MongoDB by restoring the snapshot data.
$ cat > px-mongo-snap-pvc << EOF
apiVersion: v1
kind: PersistentVolumeClaim
metadata:
name: px-mongo-snap-clone
annotations:
snapshot.alpha.kubernetes.io/snapshot: px-mongo-snapshot
spec:
accessModes:
- ReadWriteOnce
storageClassName: stork-snapshot-sc
resources:
requests:
storage: 2Gi
EOF
$ kubectl create -f px-mongo-snap-pvc.yaml
persistentvolumeclaim "px-mongo-snap-clone" created
From the new PVC, we will create a MongoDB pod.
cat < px-mongo-snap-restore.yaml >> EOF
apiVersion: apps/v1
kind: Deployment
metadata:
name: mongo-snap
spec:
strategy:
rollingUpdate:
maxSurge: 1
maxUnavailable: 1
type: RollingUpdate
replicas: 1
selector:
matchLabels:
app: mongo-snap
template:
metadata:
labels:
app: mongo-snap
spec:
affinity:
nodeAffinity:
requiredDuringSchedulingIgnoredDuringExecution:
nodeSelectorTerms:
- matchExpressions:
- key: px/running
operator: NotIn
values:
- "false"
- key: px/enabled
operator: NotIn
values:
- "false"
spec:
containers:
- name: mongo
image: mongo
imagePullPolicy: "Always"
ports:
- containerPort: 27017
volumeMounts:
- mountPath: /data/db
name: mongodb
volumes:
- name: mongodb
persistentVolumeClaim:
claimName: px-mongo-snap-clone
EOF
$ kubectl create -f px-mongo-snap-restore.yaml
deployment.extensions/mongo-snap created
Verify that the new pod is in the Running state.
$ kubectl get pods -l app=mongo-snap NAME READY STATUS RESTARTS AGE mongo-snap-6b885ddb9b-tf7zc 1/1 Running 0 5m
Finally, let’s access the sample data created earlier in the walk-through.
$ POD=`kubectl get pods -l app=mongo-snap | grep Running | grep 1/1 | awk '{print $1}'`
$ kubectl exec -it $POD mongo
MongoDB shell version v4.0.0
connecting to: mongodb://127.0.0.1:27017
MongoDB server version: 4.0.0
Welcome to the MongoDB shell.
…..
sdb.ships.find({}, {name:true, _id:false})
{ "name" : "USS Enterprise-D" }
{ "name" : "USS Prometheus" }
{ "name" : "USS Defiant" }
{ "name" : "IKS Buruk" }
{ "name" : "IKS Somraw" }
{ "name" : "Scimitar" }
{ "name" : "Narada" }
Notice that the collection is still there with the data intact. We can also push the snapshot to an Amazon S3-compatible object storage service if we want to create a disaster recovery backup in another region or location. Since Portworx snapshots work with any S3 compatible object storage, the backup can go to a different cloud or even an on-premises data center.
Summary
Portworx can be easily deployed on IBM Cloud Kubernetes Service to run stateful workloads in production. Through the integration of STORK, DevOps and StorageOps teams can seamlessly run highly available database clusters in IKS. They can perform traditional operations such as volume expansion, backup, and recovery for the cloud native applications in an automated and efficient manner.
Share
Subscribe for Updates
About Us
Portworx is the leader in cloud native storage for containers.
Thanks for subscribing!

Janakiram MSV
Contributor | Certified Kubernetes Administrator (CKA) and Developer (CKAD)Explore Related Content:
- databases
- Ibm
- iks
- kubernetes
- mongodb






