According to 2021’s CNCF annual survey, Kubernetes adoption has truly crossed the chasm of mainstream adoption, as “usage has risen across organizations globally, particularly in large businesses.” In fact, 96% of organizations this time around report they are using or evaluating Kubernetes. With the adoption of Kubernetes into many organizations today comes the exponential growth of running various business-critical applications and services on top of Kubernetes. This means valuable information is now a target for bad actors, including ransomware attacks.
“Ransomware is a type of malware that threatens to destroy or withhold a victim’s critical data unless a ransom is paid to the attacker. “ src
Ransomware attacks increased 62% from 2020 to 2021, and the average cost for such attacks was $4.62 million—and that figure does not include any ransoms that may have been paid. Kubernetes is no stranger to open-source, fast paced innovation; however, this also means that new technologies often come with potential bugs or vulnerabilities that could lead to a potential ransomware attack that could prove costly to your organization.
Farewell to Ransomware with PX-Backup
PX-Backup is an industry leader in the Kubernetes backup and recovery space, providing comprehensive enterprise data protection for Kubernetes. A few key features make PX-Backup key to any Kubernetes deployment. Application portability between clouds enables users to backup any application on any storage and restore to any other cloud or storage. Enhanced security using role based access controls and encryption provide added layers of security. Now with PX-Backup 2.2 and BaaS (backup as a service), users can gain the added benefit of ransomware protection to ease concerns over the growing number of attacks.
Key benefits of PX-Backup Ransomware Protection
- Immutability — Immutability achieved by the object lock write-once-read-many (WORM) model is the key update that enables ransomware protection for Kubernetes applications. PX-Backup discovers your backup targets that have object lock enabled and allows you to set the retention period to prevent ransomware attacks from destroying any backups. Object lock is also good for compliance and governance as well as for preventing human operator error.
- Automation of policies and schedules — PX-Backup continues to provide backup schedules and policies to allow backups to occur on a regular basis. Combine the existing power of pre- and post-backup rules with the new ransomware protection features, and PX-Backup will deliver highly secure, automated data protection at scale for your Kubernetes applications.
- Portability between any cloud — PX-Backup enabled portability for backups with block and file volumes between clouds to enable migrations of any stateful application between on-prem, hybrid, and cloud Kubernetes environments, regardless of using Portworx Enterprise. Combined with the power of immutable backups, PX-Backup gives the ultimate secure and portable backup solution for Kubernetes.
- Secure self-service — PX-Backup continues to allow organizations to authorize the users or user groups using their existing authentication service via OIDC (like Active Directory, LDAP, Okta, etc.) and map them to roles in the product. With these roles, users will have the self-service permissions to create immutable backups for their application needs.
- Ransomware support via BaaS — Built on top of the industry-leading PX-Backup, Portworx BaaS delivers speed and simplicity in data protection for your Kubernetes applications in any cloud. Users will easily gain enterprise-grade data protection with compliance support, quick disaster recovery, and ransomware protection.
How Ransomware Protection Works in PX-Backup
Create a backup location bucket with Object Lock
For this example, we will use Amazon S3 to configure S3 object lock on our backup location, though any S3-compatible object storage with object lock can be used. First, create a new bucket with a name of your choosing.
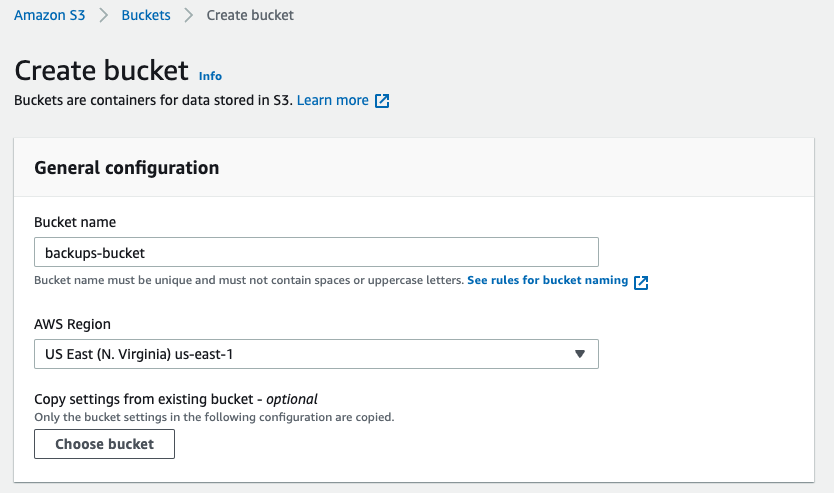
Next, scroll down to Advanced Settings and enable object lock. Then create your bucket. You will be notified that the bucket object lock needs additional configuration.
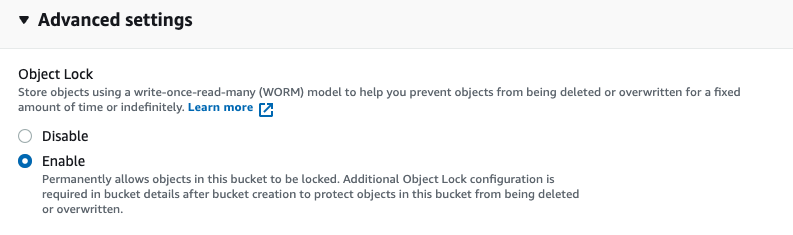
The additional configuration for retention can be found by selecting your bucket and navigating to the Properties tab and scrolling down to the object lock section. Click Edit on object lock. From here, you can select your default retention mode and what your retention period is.
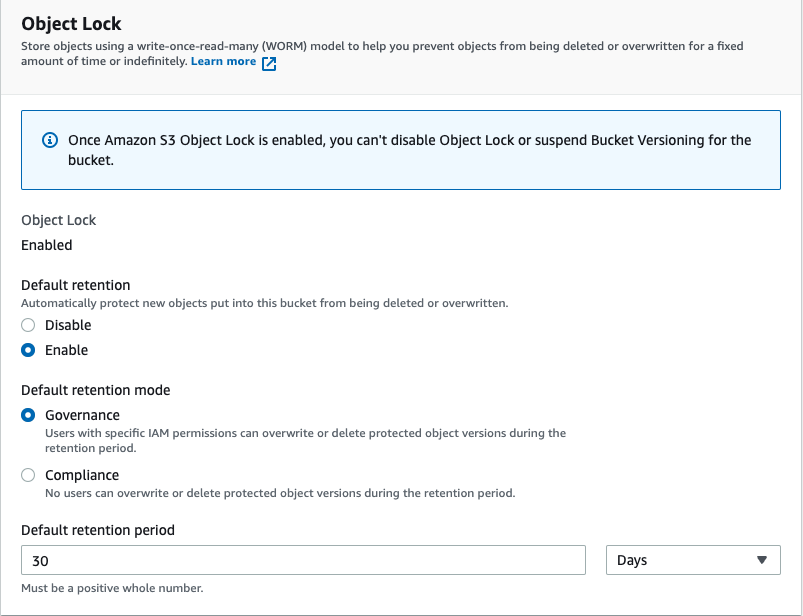
The deletion of versioned objects will add only the delete marker to object locked stored files, and the actual object version will become a non-current version. Users can invoke automation or manually delete these objects. With AWS, users can automatically clean up these delete markers and the non-current versions of the objects using a lifecycle rule within the lifecycle configuration. Navigate to lifecycle configuration, then to Create lifecycle rule, and give the rule a name.
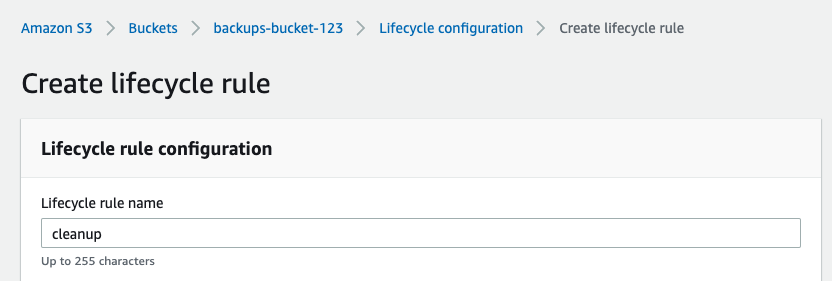
Next, select the two options below in Lifecycle rule actions and the one option in Delete expired object delete markers.
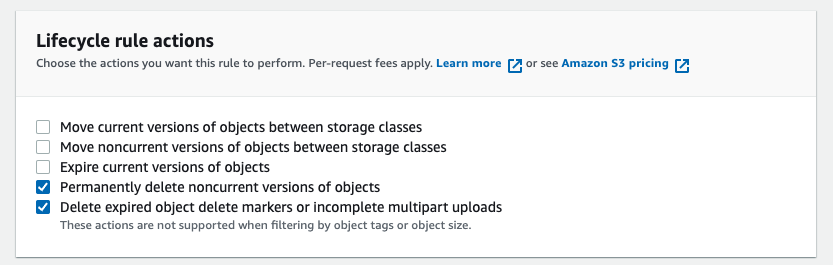
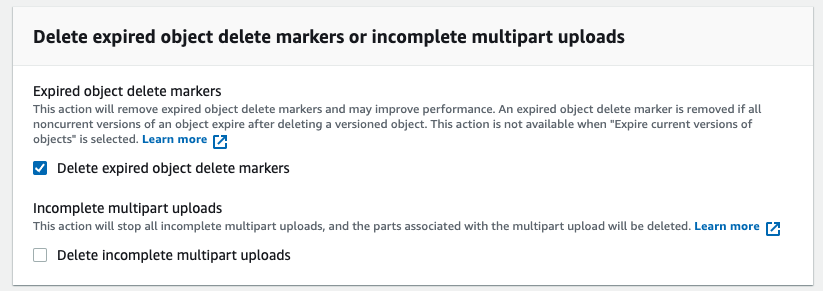
You are now ready to tell PX-Backup to use this bucket for ransomware protection.
Configure the backup location in PX-Backup
When you are creating a backup location for ransomware protection, the Path/Bucket field needs to be a previously created bucket that has object lock enabled.
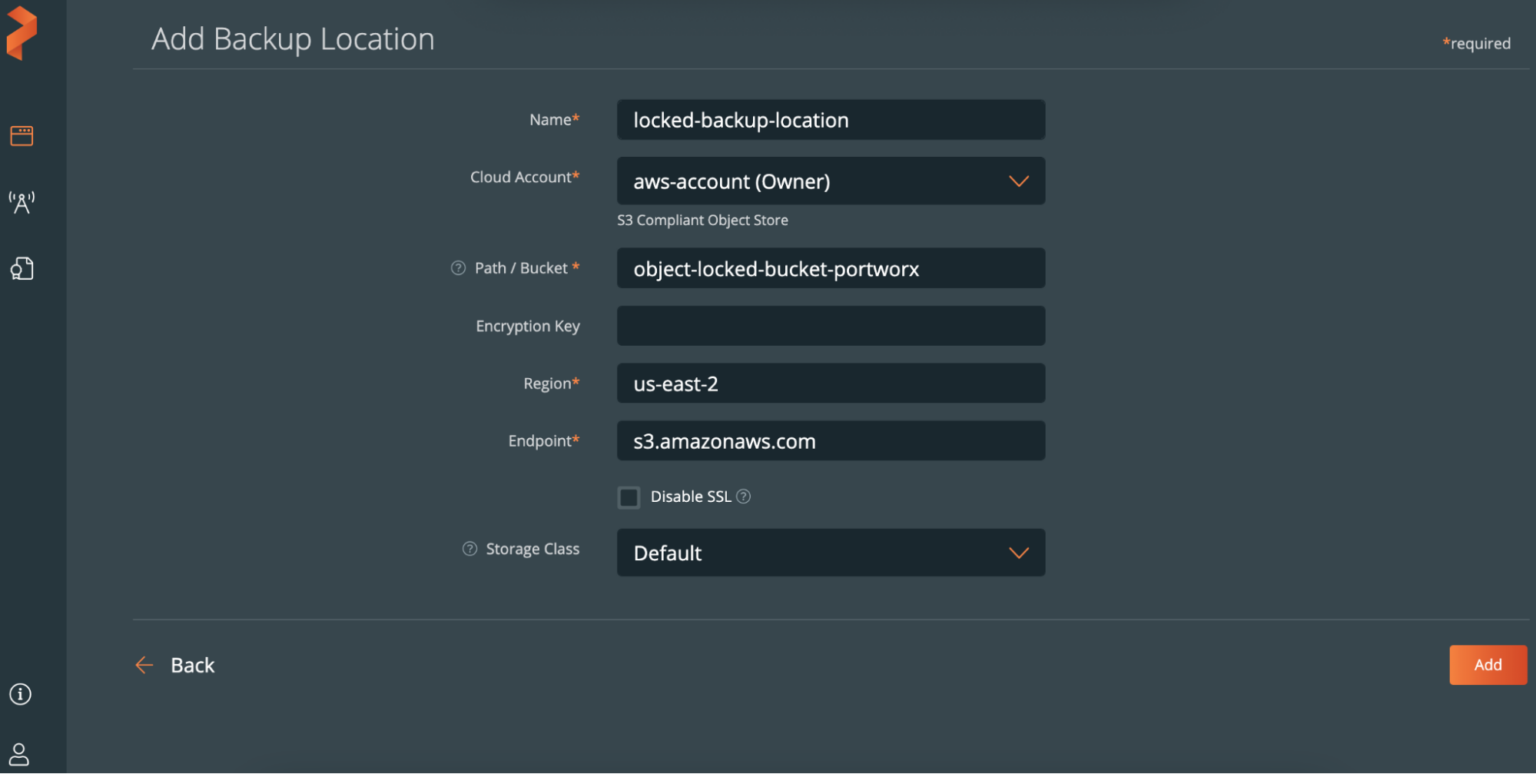
When creating a ransomware protected backup location, you will see the lock symbol in the backup location row that signifies that this is an object locked location.
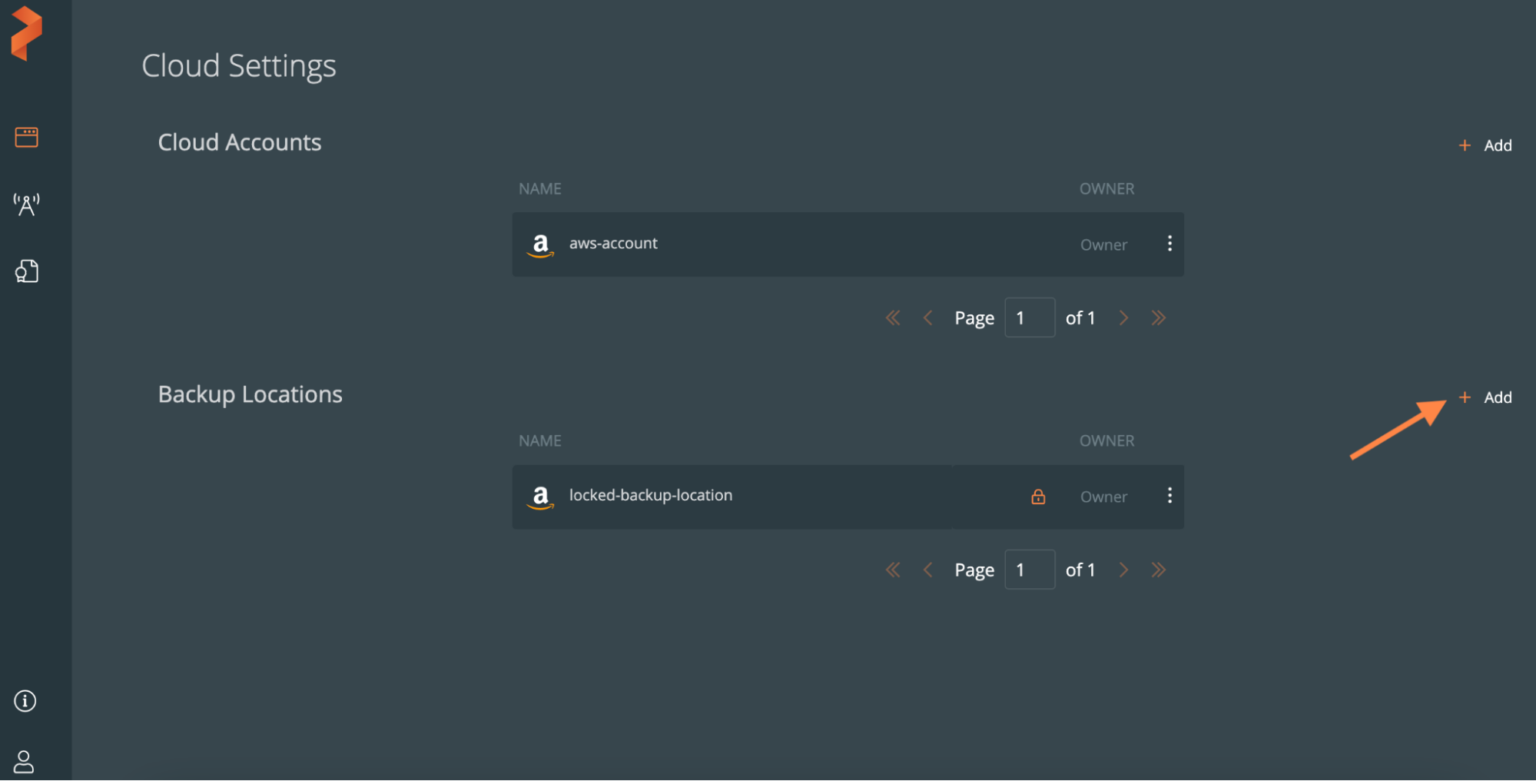
Take ad-hoc and scheduled backups that are ransomware protected
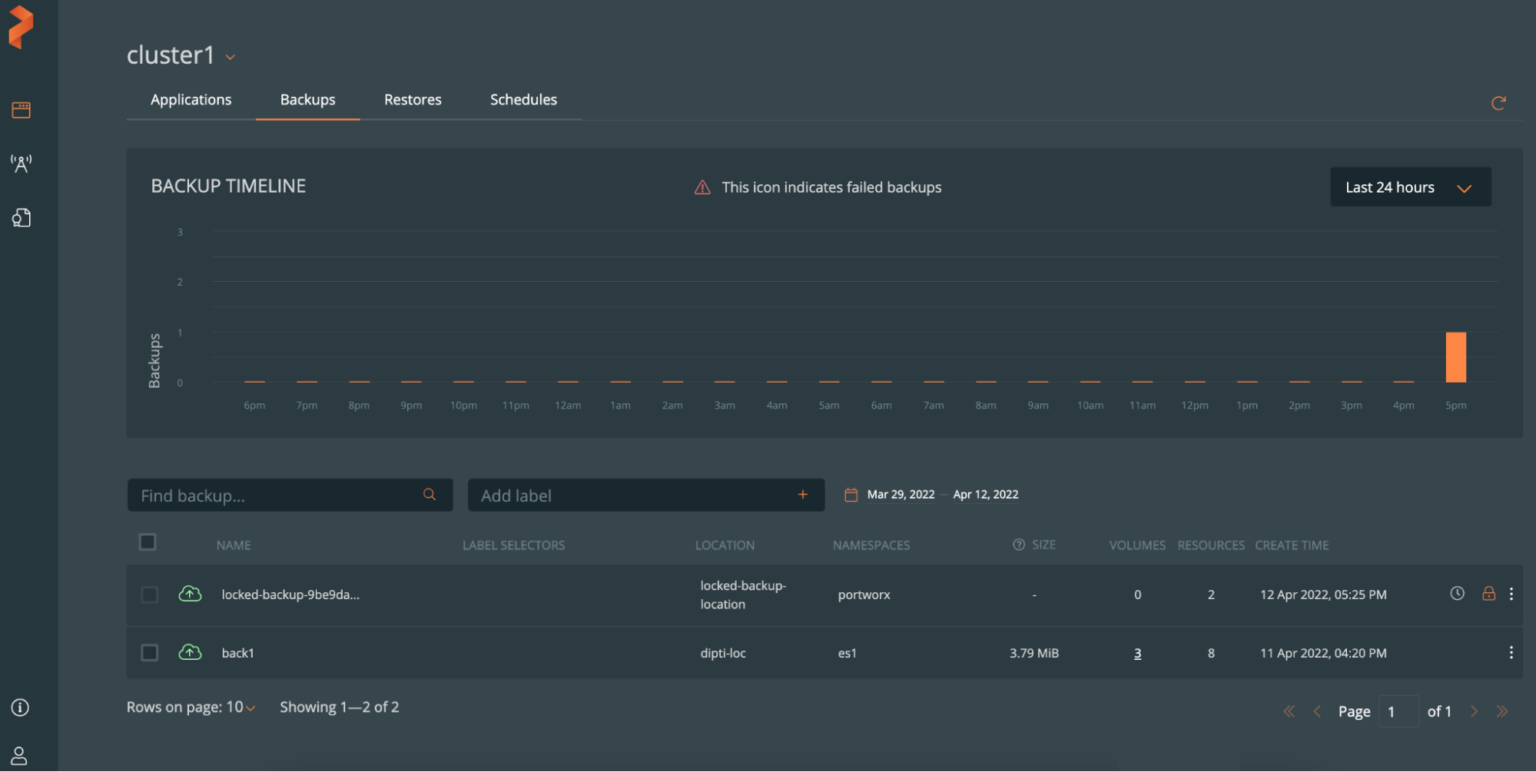
To create manual backup, create a backup as you normally would using PX-Backup. When you start the backup, you should see a lock icon indicating that it is a ransomware protected manual backup.
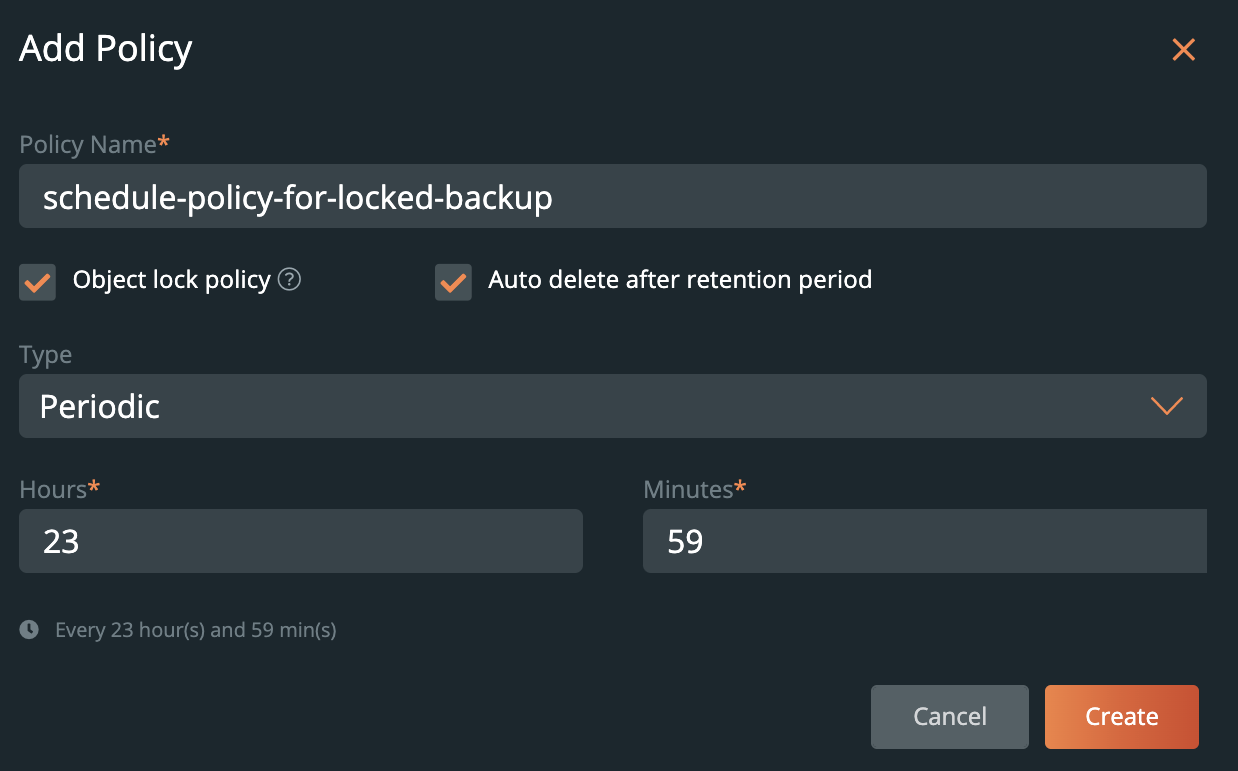
For schedule backups, users need to create a schedule policy that is used for object lock. When adding a new policy, select the Object lock policy box underneath the policy name. This will remove the manual incremental and retain selection from the policy, as this will be defaulted to what the object lock is configured to on the bucket. After this, scheduled backups can be triggered using the ransomware protected schedule policy .
Users should be aware of the following points when using object locked policies:
- Users can opt for auto-deletion. If they choose not to, deleting from the backup UI will be the user’s responsibility.
- Users can set only Periodic or Daily backups. Yearly or Monthly backups are not supported yet in the case of object lock enabled scheduled backup.
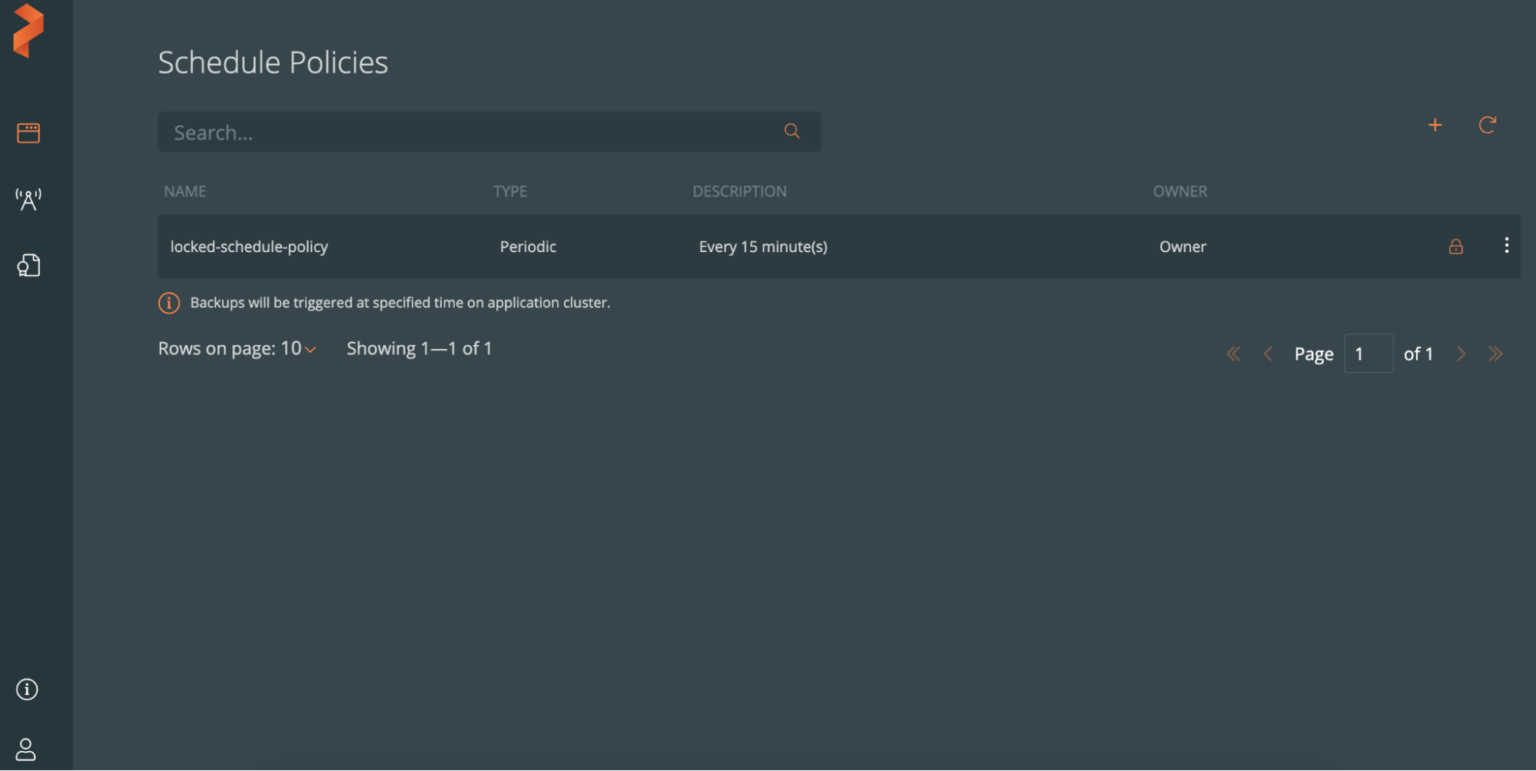
A lock icon will also appear adjacent to the new policy, as shown below.
In case of a successfully created scheduled backup using ransomware-based schedule policies, a lock icon will appear exactly as it does for manual backups. The below image shows backups taken based on a three-hour schedule policy.
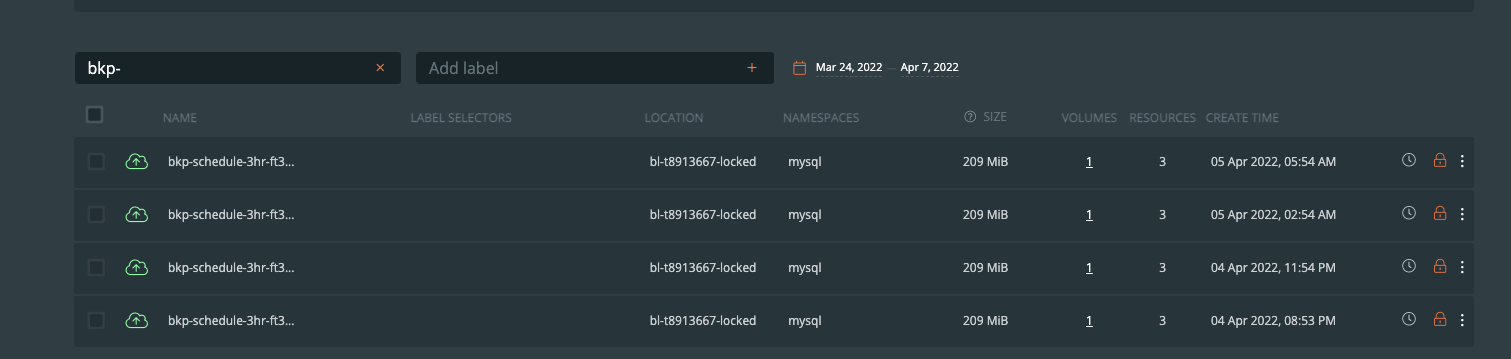
It’s important to note that with all manual backups, backups are full backups by nature of the ad-hoc request. For scheduled backups using ransomware protection, PX-Backup will take full backups after five incremental backups.
In conclusion, PX-Backup now serves as a vital way for organizations to protect their Kubernetes-based applications and data against malicious malware such as ransomware. Combining the immutability achieved by the object lock write-once-read-many (WORM) model in this latest release with the robust capabilities of role-based access control, encryption, and self service, PX-Backup can help enterprises reduce risk and gain critical efficiencies for their cloud native workflows.
Share
Subscribe for Updates
About Us
Portworx is the leader in cloud native storage for containers.
Thanks for subscribing!

Ryan Wallner
Portworx | Technical Marketing ManagerExplore Related Content:
- backup
- data protection
- database
- kubernetes
- malware
- protect
- protection
- ransomware
- restore
- stateful